https://doi.org/10.1140/epjqt/s40507-024-00295-1
Research
Quantum differential cryptanalysis based on Bernstein-Vazirani algorithm
1
School of Computer and Big Data (School of Cybersecurity), Heilongjiang University, 150080, Harbin, China
2
School of Mathematical Science, Heilongjiang University, 150080, Harbin, China
3
School of Computer Science (National Pilot Software Engineering School), Beijing University of Posts and Telecommunications, 100876, Beijing, China
Received:
29
April
2024
Accepted:
3
December
2024
Published online:
18
December
2024
Recent research has demonstrated the potential of quantum algorithms to exploit vulnerabilities in various popular constructions, such as certain block ciphers like Feistel, Even-Mansour, and multiple MACs, within the superposition query model. In this study, we delve into the security of block ciphers against quantum threats, particularly investigating their susceptibility to cryptanalysis techniques, notably exploring quantum adaptations of differential cryptanalysis. Initially, we introduce a BV-based quantum algorithm for identifying linear structures with a complexity of 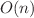 , where n denotes the number of bits in the function. Subsequently, we illustrate the application of this algorithm in devising quantum differential cryptanalysis techniques, including quantum differential cryptanalysis, quantum small probability differential cryptanalysis, and quantum impossible differential cryptanalysis, demonstrating polynomial acceleration compared to prior approaches. By treating the encryption function as a unified entity, our algorithm circumvents the traditional challenge of extending differential paths in differential cryptanalysis.
, where n denotes the number of bits in the function. Subsequently, we illustrate the application of this algorithm in devising quantum differential cryptanalysis techniques, including quantum differential cryptanalysis, quantum small probability differential cryptanalysis, and quantum impossible differential cryptanalysis, demonstrating polynomial acceleration compared to prior approaches. By treating the encryption function as a unified entity, our algorithm circumvents the traditional challenge of extending differential paths in differential cryptanalysis.
Key words: Block cipher / Differential cryptanalysis / Quantum cryptanalysis / BV algorithm
© The Author(s) 2024
 Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.





